Stop Echoing Batman's Secrets
CICDInstead of echoing your secrets in your actions use the official Github Google Cloud Action
Dick has moved on to be Nightwing; Jason is dead-ish; Tim has decided to explore his other passions and now it's finally your shot to be Batman's sidekick and you can't shut up about it. So much so that you echo -ed the secrets to the Batcave! Get it?

Here’s a real-world example I’ve seen floating around:
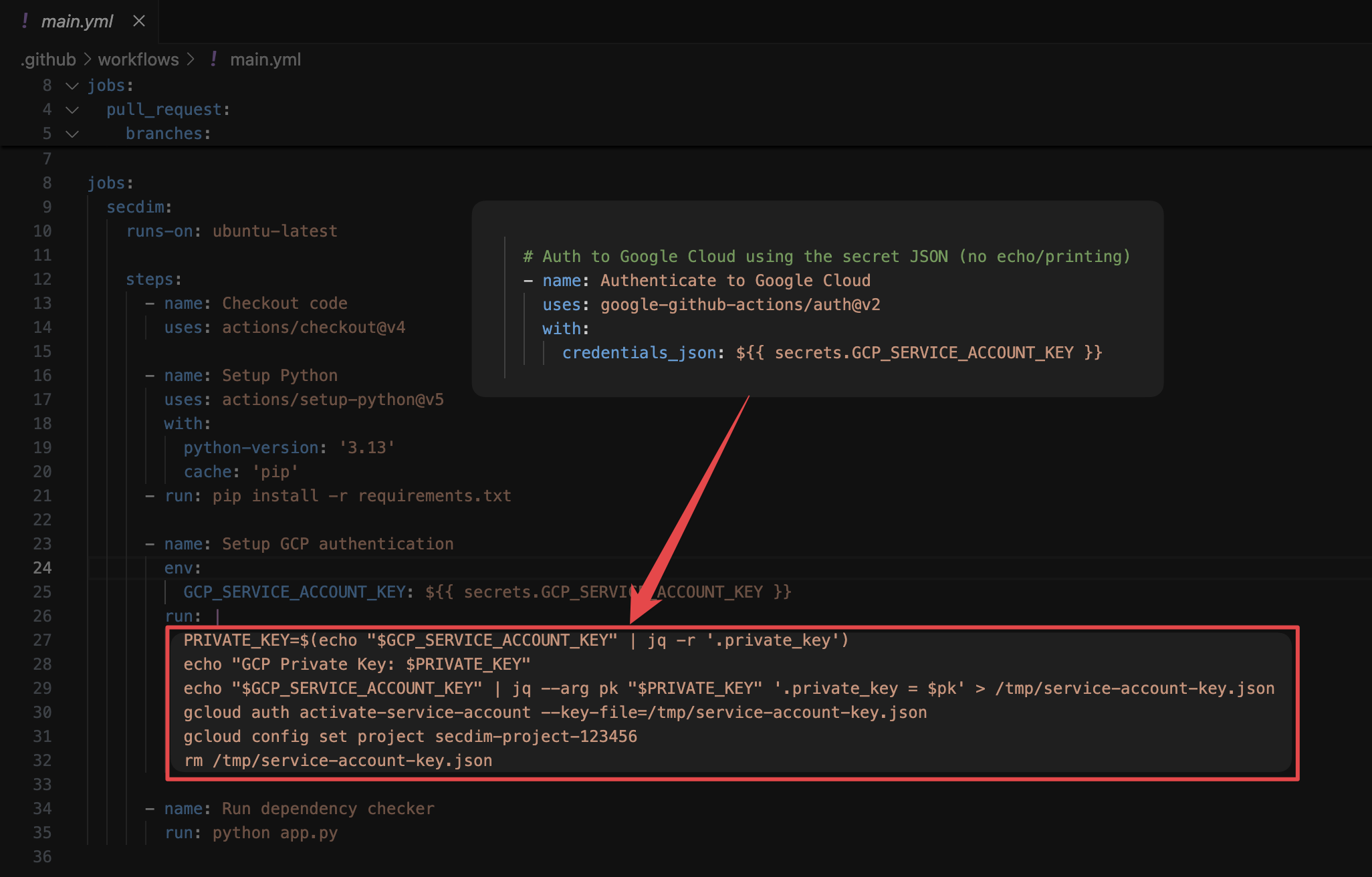
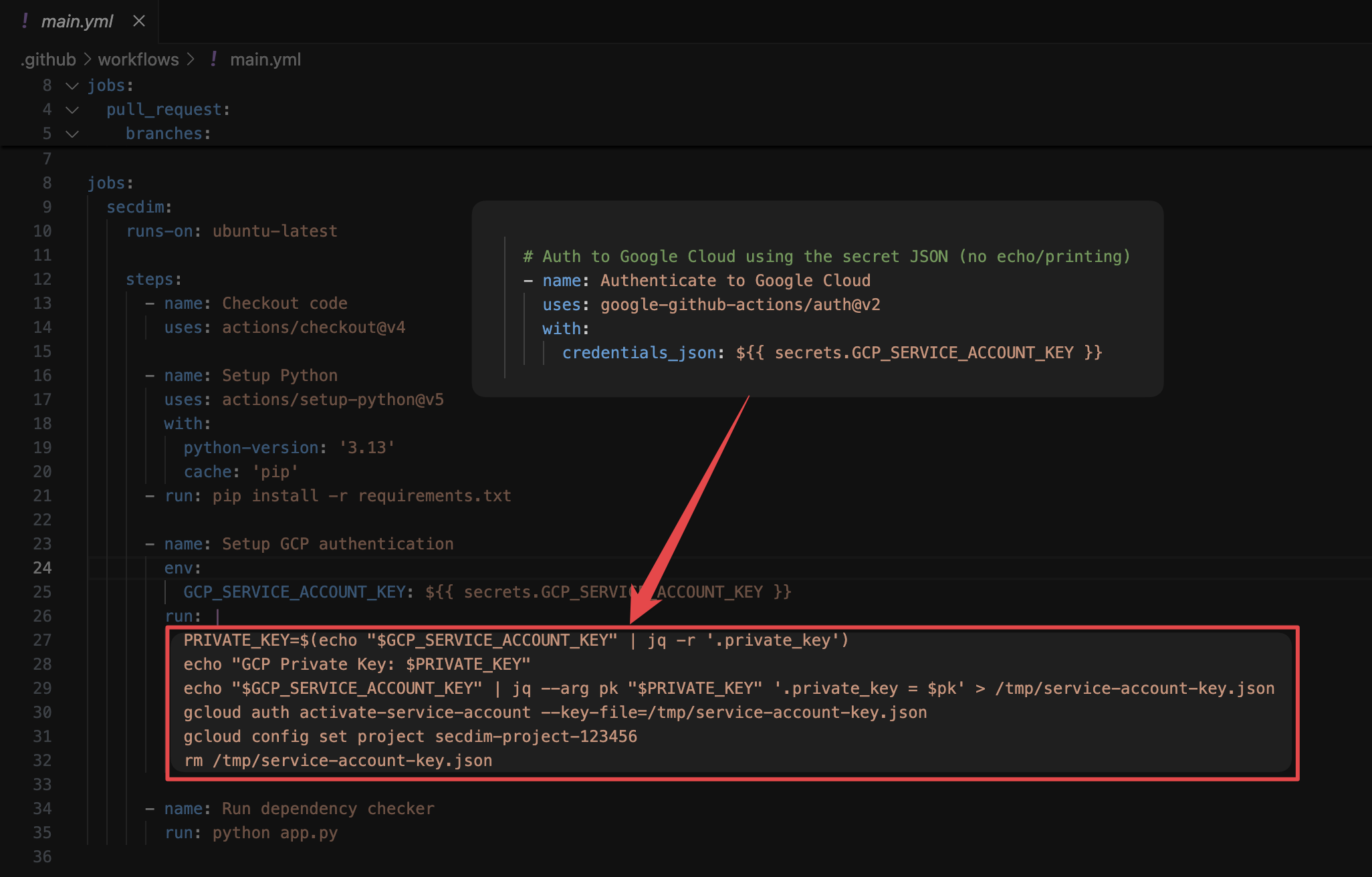
- name: Setup GCP authentication
env:
GCP_SERVICE_ACCOUNT_KEY: ${{ secrets.GCP_SERVICE_ACCOUNT_KEY }}
run: |
PRIVATE_KEY=$(echo "$GCP_SERVICE_ACCOUNT_KEY" | jq -r '.private_key')
echo "GCP Private Key: $PRIVATE_KEY"
echo "$GCP_SERVICE_ACCOUNT_KEY" > /tmp/service-account-key.json
gcloud auth activate-service-account --key-file=/tmp/service-account-key.json
Yes, it works.
Yes, your CI/CD pipeline is green.
But congrats, you’ve also broadcast your private key to anyone who can read the workflow logs.
Why This Is Bad (Besides Batman’s Wrath)
- GitHub’s masking only protects exact secret strings, not transformed ones
- CI logs often outlive the secrets themselves
- Anyone with repo access can replay that key
It’s like writing your ATM PIN on the back of your debit card because “hey, it works.”
What Would Batman Do
- Use the official
google-github-actions/authaction 🦇: https://github.com/google-github-actions/auth
- name: Authenticate to Google Cloud
uses: google-github-actions/auth@v2
with:
credentials_json: ${{ secrets.GCP_SERVICE_ACCOUNT_KEY }}
- name: Setup gcloud CLI
uses: google-github-actions/setup-gcloud@v2
- name: Configure gcloud project
run: gcloud config set project secdim-project-123456
✅ No temp files.
✅ No echoes.
✅ No “oops I leaked prod creds in a demo.”
Batman Would Also
- Mask everything in logs like it’s his true identity
- Rotate keys faster than he rotates Robins
- Only grant the least privilege (because why would Gotham’s coffee machine need
roles/owner?) - And of course, set up a bat-signal alert if a secret ever leaked
TL;DR
- Don’t echo secrets. Not even “just for debugging.”
- Use official actions for cloud authentication.
- Remember: Logs are forever, but secrets should never be.
One More Thing
You can in fact run Github Actions locally with ACT
Useful for testing purposes 🧪



Comments