My first real cybersecurity conference/event in Florida was B-Sides Tampa. It was hosted at University of South Florida (USF), The Muma College of Business.



Vendors, Panels, and Unicorns?
It was honestly pretty cool talking to all the vendors and learning about the different products and services out there. I never really felt like anyone was overly trying to sell me anything. If anything they were just trying to be as helpful as possible. Everyone was super friendly too!
There were a few GRC-esk panels. Nothing against any of the speakers but I'm personally not really keen on these panels because I always feel like its sort of useless (or rather not actionable) thought leadership 😅. But I'm always hopeful that someone will change my mind one day and thats why I keep poking my head in.







Tracks
Unfortunately I didn't have Hermione's Time Turner, so I couldn't attend all the tracks but I biased towards the offensive stuff and tried to poke my head in as much of the other stuff as possible.





Conference Laptop Updates
I got some cool stickers to add to my old dell latitude lab pc! This dell laptop was my first "lab machine" when I couldn't afford much and I put it together via Ebay parts for under $200.

Pentesting AWS
I was determined to not miss this talk from Mike Felch of Black Hills Infosec. Maybe it's my loathing for Active Directory or maybe it's genuine interest on how to hack cloud environments. Either way it was a great talk on enumerating and highlighting some assumptions about AWS.

I think every time there is a "new-ish" technology it suffers from these quiet assumptions that people make about it. I think it's the job of security engineers to focus on those assumptions and shine a light on them to see what's really what.



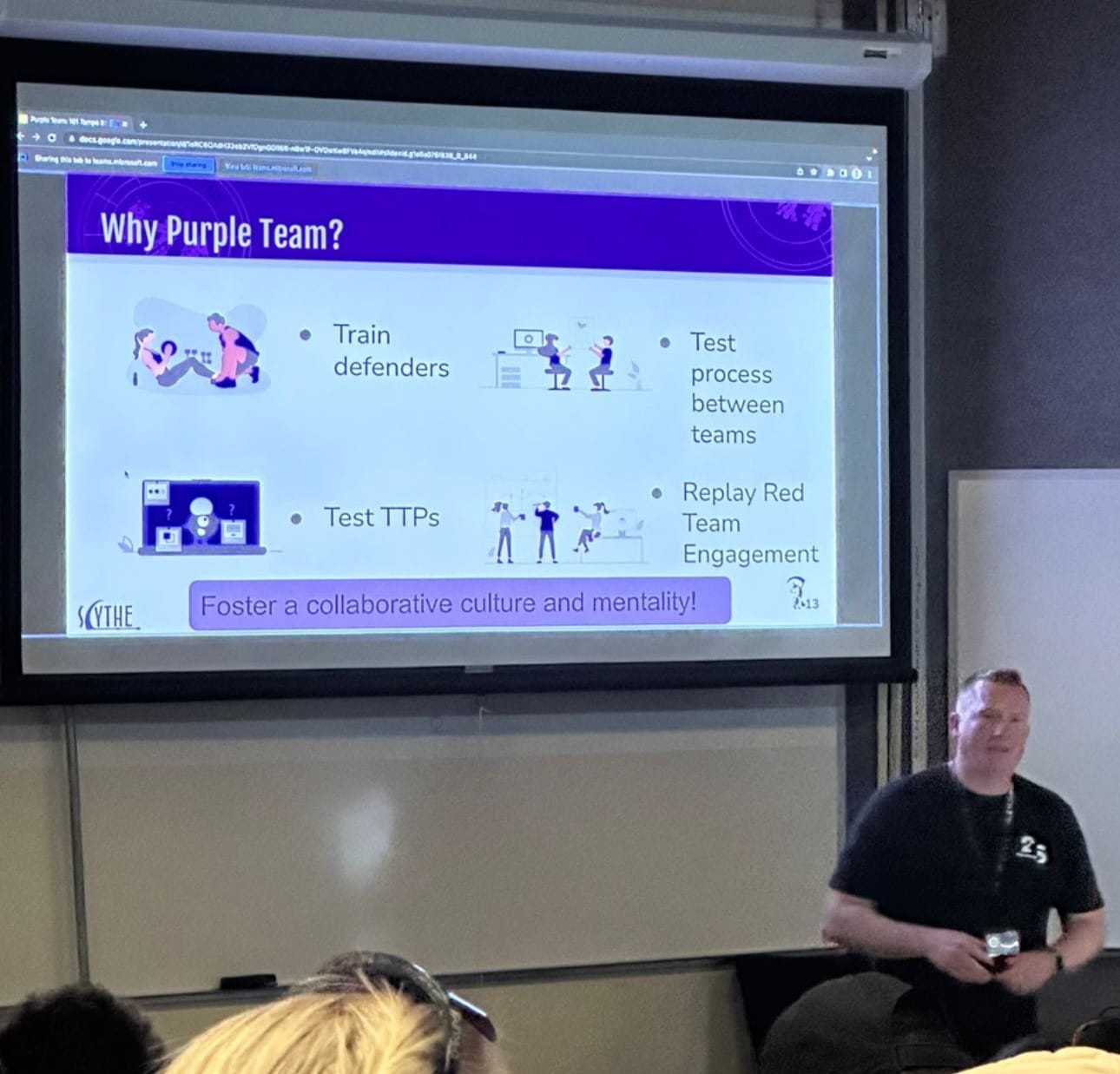
Purple Team
This was a more blue-team leaning talk and I believe it even was on the security operations (blue-team) track. Bucketing aside, it was a very interesting idea to me. Usually blue and red teams just sort of do their own thing. Those teams run their services, complete their jobs, generate their reports, share their findings and then they are on their separate ways in life. But purple team involves a lot of collaboration and tuning of the blue team by being more interactive with the red teamers to process improve.
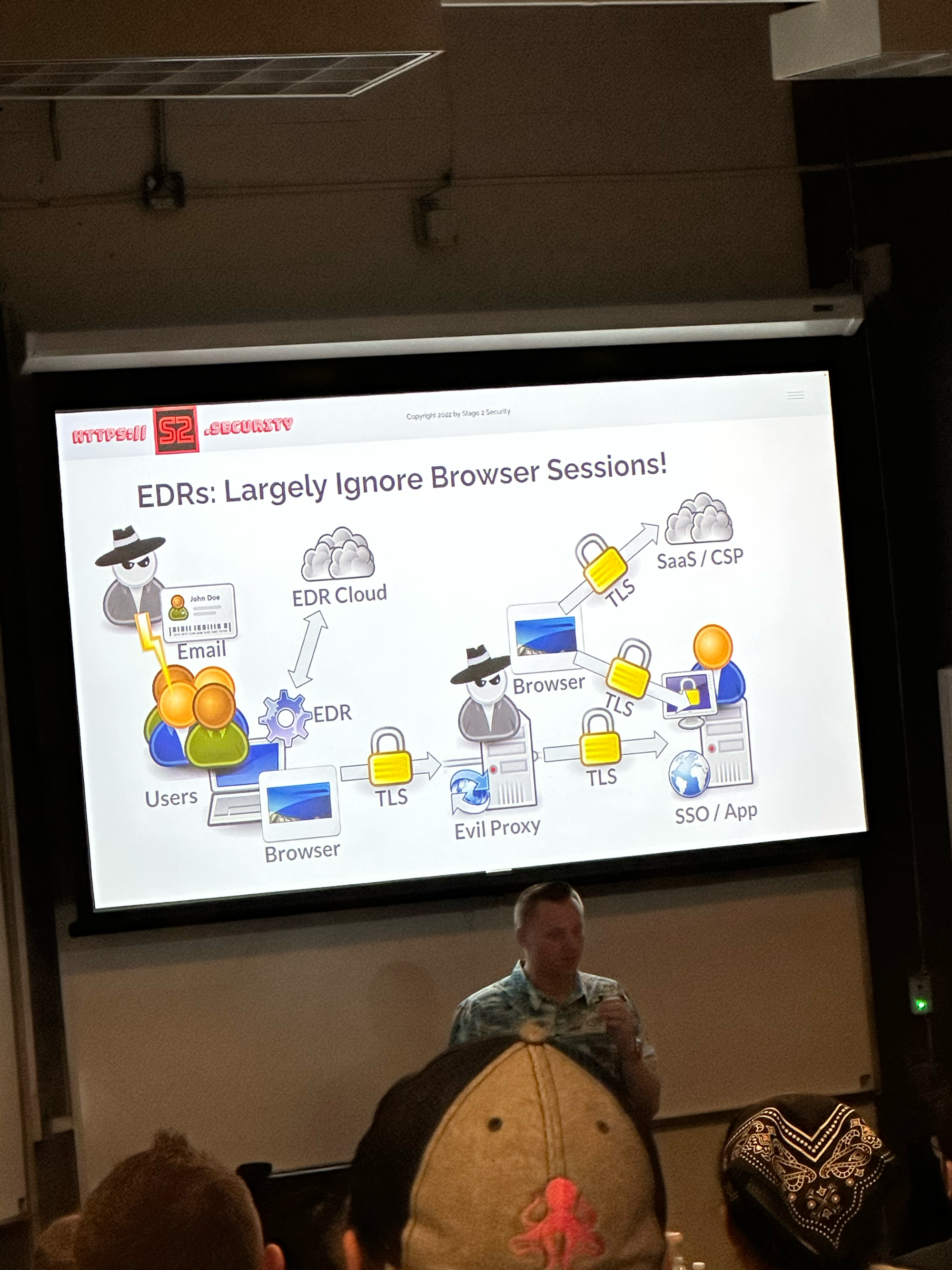
Cloud Red Teaming: Initial Access & Priv Esc

This was a very interesting talk but the thing that stuck out to me the most was just how vulnerable browser extensions could be. It seemed that browser extensions would be the perfect vector for doing some real damage. This also reminded me of how powerful BeEF could be on an engagement.

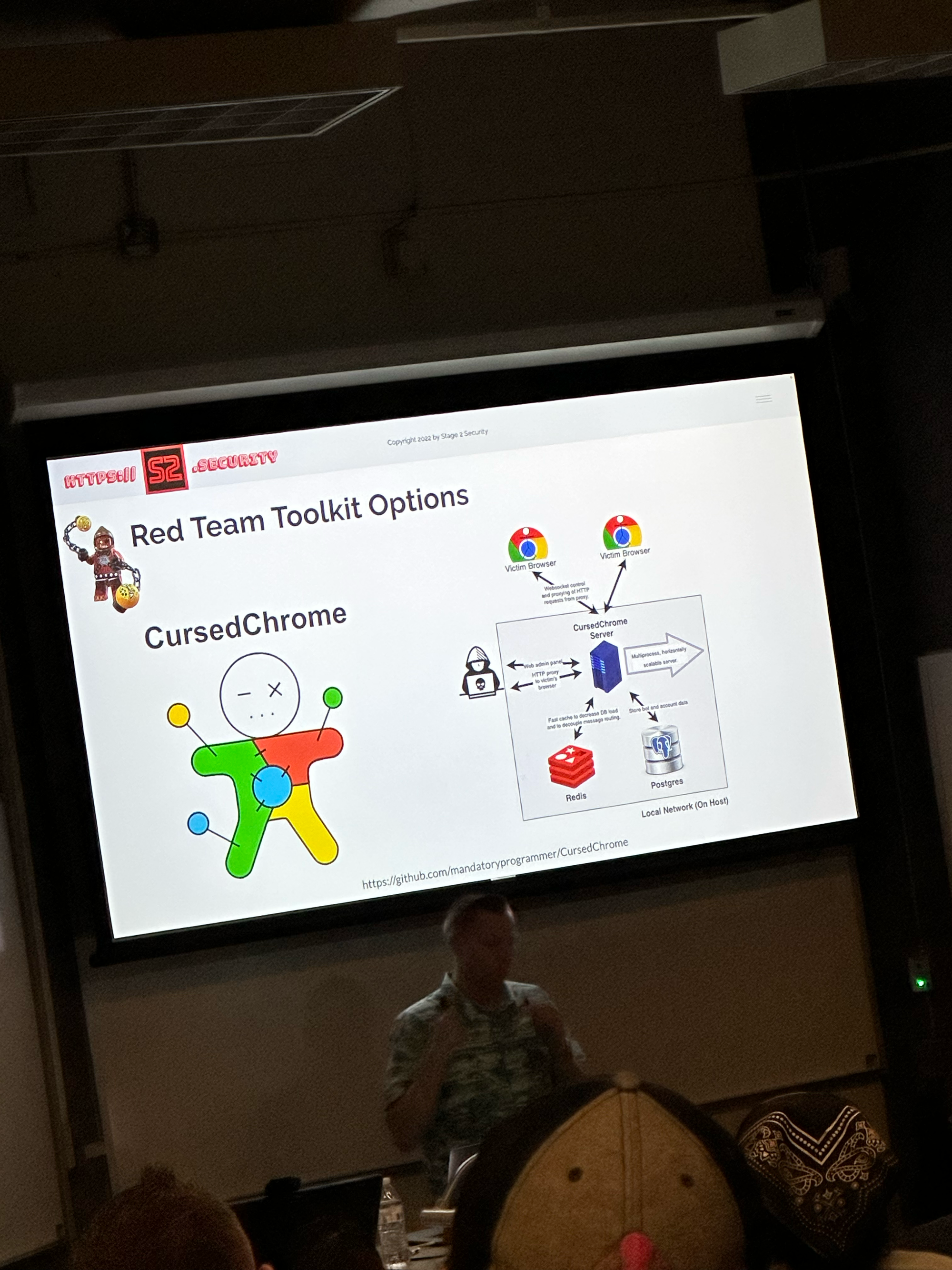
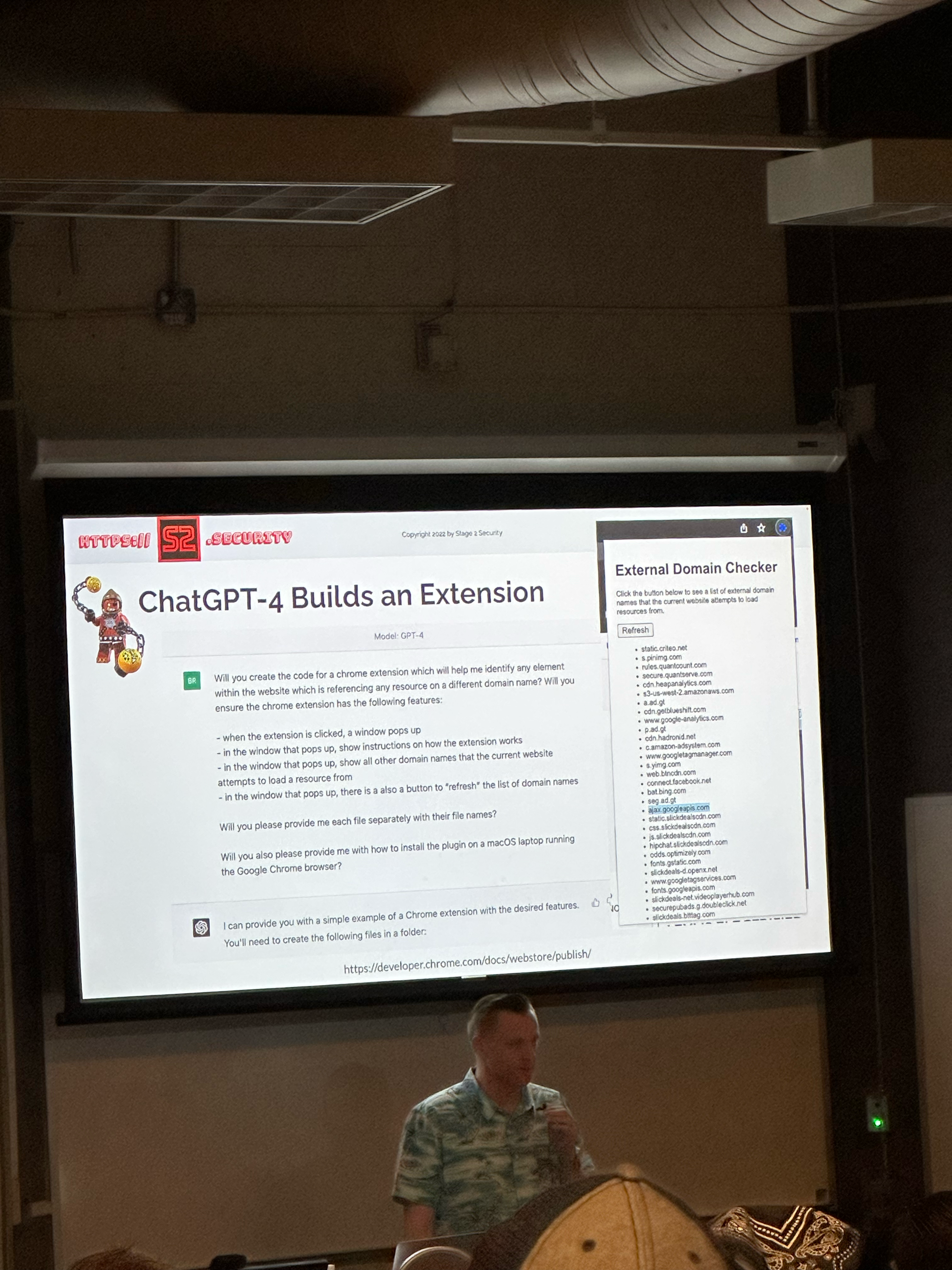
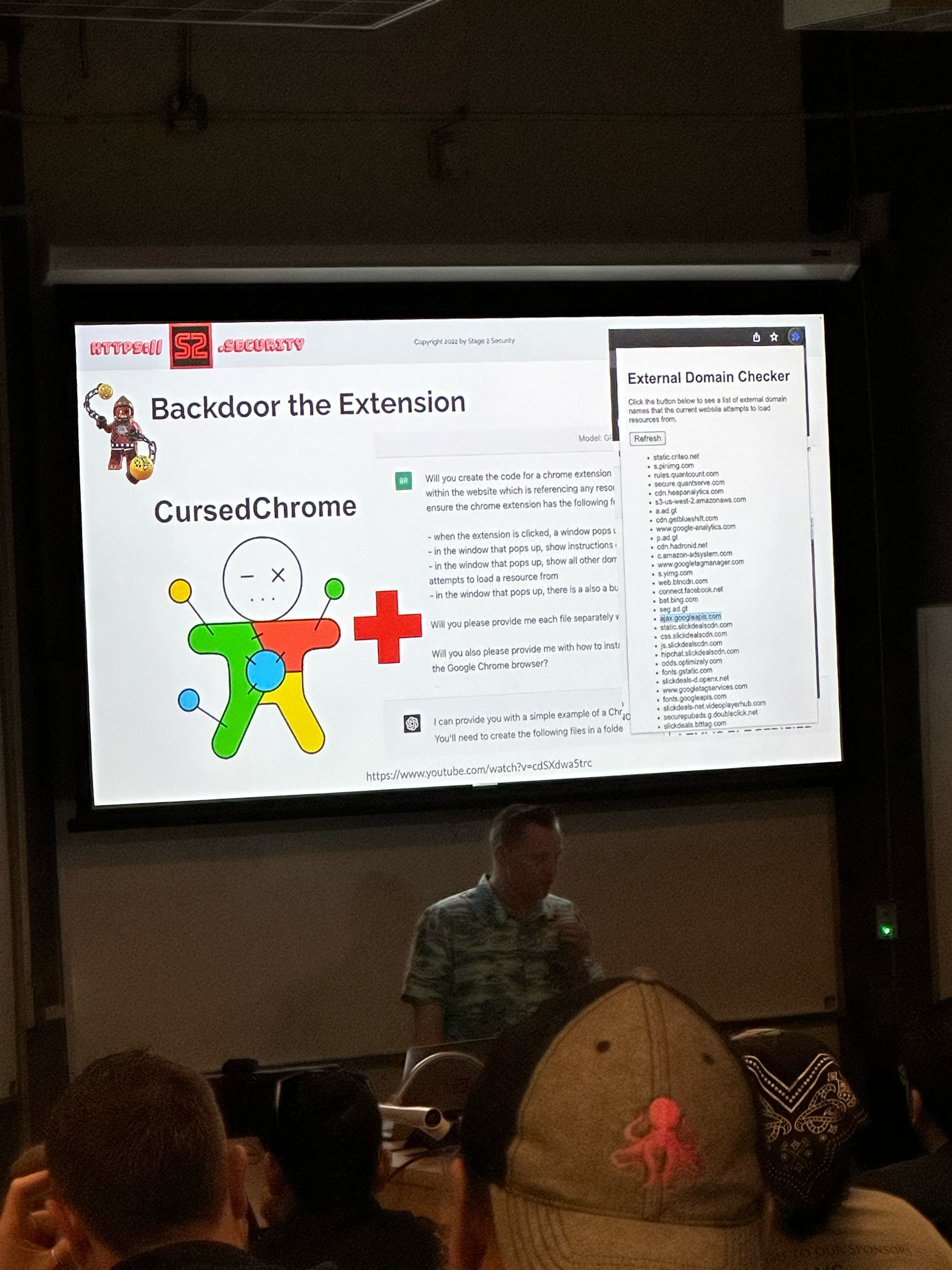

Close Out, Happy Hour, and Wow Florida
I met some really awesome people here. AWS even sponsored the after party/ happy hour. I don't really drink 😅 but it was nice to further connect with all the people I could in the Tampa cybersecurity scene. I was wholly surprised to learn about all the cybersecurity companies that are actually based in Florida. It'll be an exciting next few years I think.






My First "Cool" Conference Badge
Oh yeah! Almost forgot about this part.





